You have a cyber security strategy, now what?
After the Board has agreed to a suitable cyber strategy (Read: How to Develop a Cyber Security Strategy at the Board-Level) which complies with all relevant regulation and has been embedded into the governance framework, it must now turn its attention to implementing this strategy throughout the organization.
A cyber security governance framework contains a set of management tools, a comprehensive risk management approach and, more importantly, an organization-wide security awareness program. This framework should weave into your organization’s key systems and processes from end to end.
By this stage, you should have identified your Crown Jewel assets, and organized a risk register which identifies the potential risks which require treatment (a bit more information on this area can be found here).
Filling out a cyber risk register will help you recognize potential risks, determine the costs for those risks, and provide answers to what you can do to help prevent them before they happen.
With the risk register in hand, begin by assessing the tactical plans developed by senior management and determine a suitable budget for cyber security.
An important consideration when determining budget allocation is the return on investment; not all assets are worthy of the same level of funding, just as some risks are more urgent than others. The protection of your critical assets should receive more weight in the proposed budget.
Your critical assets, also known as the Crown Jewels, may include any or all of the following:
Client, donor or trustee data (usernames, email addresses, physical addresses, passwords, bank information, financial records, healthcare information, confidential email threads etc.)
Sensitive contracts with customers, suppliers, distributors, joint venture partners etc.
Employee log-in credentials
Business plans
New products or services in development
Lists of customers, employees or contractors
If the idea of allocating a dedicated cyber security budget seems extreme, especially when you haven’t traditionally needed one, it should be noted some estimates place the average cost of a data breach in Australia, for example, at $5.4 million AUD. Penalties for breaches of privacy under the Australian Privacy Act now exceed $340,000 AUD. This is similar in many countries.
How much would a data breach cost you? Explore IBM's analysis tool by scrolling down and selecting your country.
Some studies have shown 60 percent of Australian business are forced to close within six months following a cyber attack. These statistics are immediately translatable to other countries, with more legislation mandating fines for failing to manage cyber security or deal appropriately with its aftermath.
Cyber attacks are relatively inexpensive to mount yet highly profitable, which means its likely these attacks will only increase in frequency and reach. The Board needs to ensure that management is fully engaged in making the organization’s systems as resilient as economically feasible in the face of this onslaught.
When resource capabilities are limited, consider a finding from the Australian Signals Directorate that suggests the following four strategies could have been used to thwart 85 percent of detected intrusions:
Prevent malicious software and unapproved programs from running by restricting the programs that can run on your system (“Whitelisting”)
Continually patch software applications such as Flash, web browsers, Microsoft Office, Java and PDF viewers
Ensure the operating systems are patched with current updates
Restrict administrative privileges (the ability to change settings or install software)
While these preventative strategies are mandatory for many Government organizations, they cannot be the only defense against the full spectrum of cyber threats. Ensuring the cyber security framework receives wide adoption across your organization and suitable funding is one way to do this.
Board subcommittee reporting
When rolling out a cyber security framework, it is important to establish an ongoing feedback loop which allows reporting on the effectiveness of cyber security measures to filter back to the Board for assessment.
Establishing a Finance Audit Risk Management and Security (FARMS) committee or similar infrastructure can aid this process. Most commonly, Security is been added to the already existing Finance/Audit/Risk Board committee. The FARMS committee reports back to the Board on the effectiveness of the cyber security strategy, with reference to any new regulatory obligations, and associated planning. This committee provides recommendations to the Board on matters specific to cyber security, but it does not authorize any activities by itself.
The composition of the FARMS committee may include the Chief Financial Officer, at least one director, an external independent strategic finance specialist, the risk manager and a cyber security expert or individual with similar technical expertise. As organizations now face new threats, seemingly from all sides, it has become increasingly important to bring knowledgeable perspectives on cyber security matters into the Boardroom, including through the committee structure.
Briefings from independent third-party experts or external auditors should be considered by the Board to verify the cyber strategy and provide an industry-wide perspective on emergent cyber-risk trends.
It is crucial for Directors to do more than simply receive reports from management; they must approach cyber security as a business problem with technology integrations. The same principles of inquiry used during financial reporting should apply.
With the help of the FARMS committee, cyber-intelligent governance should include updates on specific industry risks and mitigation strategies, as well as reports about the organization’s overall cyber security program. This could include determining what to disclose in the event of a cyber attack.
Keep your personal security front of mind
Board members must now take an active role in educating themselves on their role and the Board's responsibility in the protection of valuable assets and sensitive information.
It’s also important to understand that Board members of high profile organizations are prime candidates for a spear phishing campaign ─ a targeted attack from a hacker ─ so additional caution when online should be exercised at all times.
A few practical ways to ensure your personal details remain secure may include:
Use modern and up-to-date antivirus software on your computer
Don’t use your personal email for sensitive correspondence (typical providers such as Gmail and Yahoo have both been hacked in recent years).
Be cautious of free WiFi in public places
Think about how much information you make available about yourself online
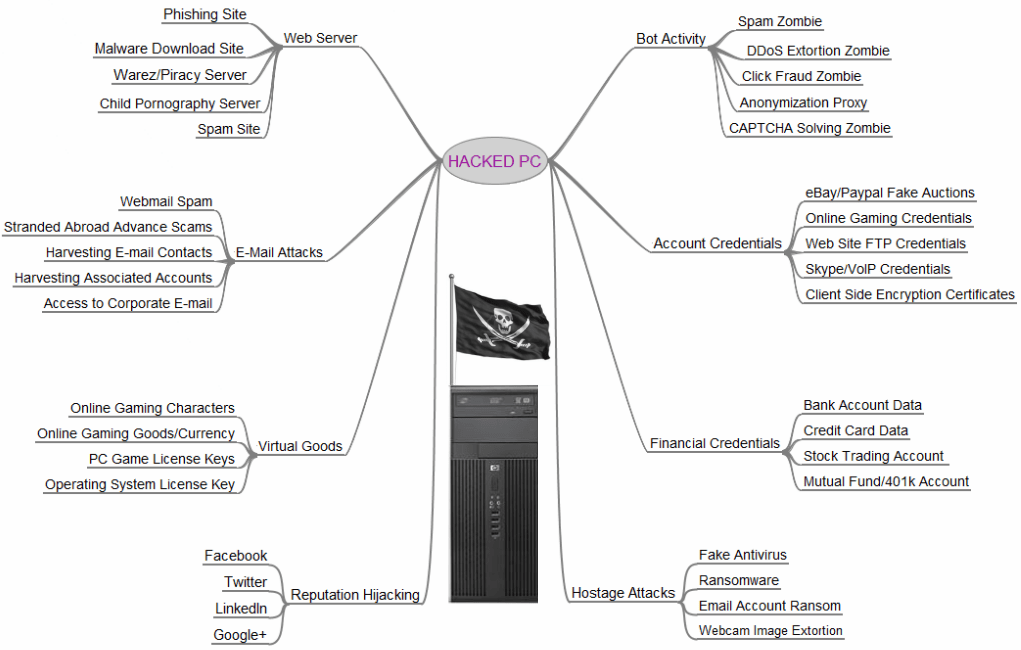
If you think you have nothing worth stealing, think again. The following diagram shows a few of the many ways your identity can be monetized.
"One of the ideas I tried to get across with this image is that nearly every aspect of a hacked computer and a user’s online life can be and has been commoditized. If it has value and can be resold, you can be sure there is a service or product offered in the cybercriminal underground to monetize it. I haven’t yet found an exception to this rule."
-- Brian Krebs, journalist and computer security expert.
Image via Krebs on Security
Lastly, Board members and senior management are uniquely positioned to champion a culture of cyber security training and awareness. Employees in an organisation must be aware of the potential threats they could face, whether it’s a phishing email, sharing passwords or using an insecure network.
The cyber security landscape is always changing as hackers find new ways to access information, which is why creating a culture of consistent awareness of threats is so important.